Cyber Security. Simplified. For Creators.
Helping Creators Grow Securely is what We Do!
Helping Creators Grow Securely is what We Do!







Data breaches at social media platforms and creator tools can expose creators' personal information and audience data
Social engineering tactics like phishing emails and fake DMs can trick creators into revealing sensitive information or compromising their accounts
Investing in cybersecurity tools and education is essential for creators to protect themselves and their online communities
Common ways by which creators Gets Hacked ?
Common ways by which creators Gets Hacked ?
By understanding creators' behaviors, hackers aim to breach accounts, manipulate content, or extract valuable data. they gather publicly available data to craft convincing phishing messages, impersonate creators, or guess security questions to gain unauthorized access.
By understanding creators' behaviors, hackers aim to breach accounts, manipulate content, or extract valuable data. they gather publicly available data to craft convincing phishing messages, impersonate creators, or guess security questions to gain unauthorized access.

Sponsorship Scams

Sponsorship Scams

Sponsorship Scams

Sponsorship Scams

Identity Theft

Identity Theft

Identity Theft

Identity Theft



Data Breach sold over darkweb










Why are creators on aim?
Why are creators on aim?
Creators, due to their visibility, impact, and often lucrative online presence, become alluring targets for hackers with various motives.
Creators, due to their visibility, impact, and often lucrative online presence, become alluring targets for hackers with various motives.

Large follower base & Impact

Large follower base & Impact

Large follower base & Impact

Large follower base & Impact

Demand hefty amount of ransom

Demand hefty amount of ransom

Demand hefty amount of ransom

Demand hefty amount of ransom

Suppress creators in the same field

Suppress creators in the same field

Suppress creators in the same field

Suppress creators in the same field
Online Threats That exists

Impersonations
Shield your brand and personal identity from malicious impersonation attempts, preserving your reputation and trustworthiness.

Impersonations
Shield your brand and personal identity from malicious impersonation attempts, preserving your reputation and trustworthiness.

Impersonations
Shield your brand and personal identity from malicious impersonation attempts, preserving your reputation and trustworthiness.

Impersonations
Shield your brand and personal identity from malicious impersonation attempts, preserving your reputation and trustworthiness.

Spam Accounts
Safeguard your online spaces from spam accounts, ensuring genuine interactions and maintaining brand integrity

Spam Accounts
Safeguard your online spaces from spam accounts, ensuring genuine interactions and maintaining brand integrity

Spam Accounts
Safeguard your online spaces from spam accounts, ensuring genuine interactions and maintaining brand integrity

Spam Accounts
Safeguard your online spaces from spam accounts, ensuring genuine interactions and maintaining brand integrity

Deep Fake Ads
Counter the threat of deep fake advertisements, protecting your brand potential reputational damage.

Deep Fake Ads
Counter the threat of deep fake advertisements, protecting your brand potential reputational damage.

Deep Fake Ads
Counter the threat of deep fake advertisements, protecting your brand potential reputational damage.

Deep Fake Ads
Counter the threat of deep fake advertisements, protecting your brand potential reputational damage.

Dark web Exposures
Proactively monitor dark web exposures, preventing attacks such as credential stuffing which Leads to Account takeover

Dark web Exposures
Proactively monitor dark web exposures, preventing attacks such as credential stuffing which Leads to Account takeover

Dark web Exposures
Proactively monitor dark web exposures, preventing attacks such as credential stuffing which Leads to Account takeover

Dark web Exposures
Proactively monitor dark web exposures, preventing attacks such as credential stuffing which Leads to Account takeover

Leaked Credential Monitoring
Keeps an eye on leaked credentials, fortifying your accounts and ensuring early detection to prevent unauthorized access

Leaked Credential Monitoring
Keeps an eye on leaked credentials, fortifying your accounts and ensuring early detection to prevent unauthorized access

Leaked Credential Monitoring
Keeps an eye on leaked credentials, fortifying your accounts and ensuring early detection to prevent unauthorized access

Leaked Credential Monitoring
Keeps an eye on leaked credentials, fortifying your accounts and ensuring early detection to prevent unauthorized access

Misuse of Intellectual Property
Swiftly and effectively respond to brand infringement with our takedown solutions, maintaining control over your digital presence.

Misuse of Intellectual Property
Swiftly and effectively respond to brand infringement with our takedown solutions, maintaining control over your digital presence.

Misuse of Intellectual Property
Swiftly and effectively respond to brand infringement with our takedown solutions, maintaining control over your digital presence.

Misuse of Intellectual Property
Swiftly and effectively respond to brand infringement with our takedown solutions, maintaining control over your digital presence.
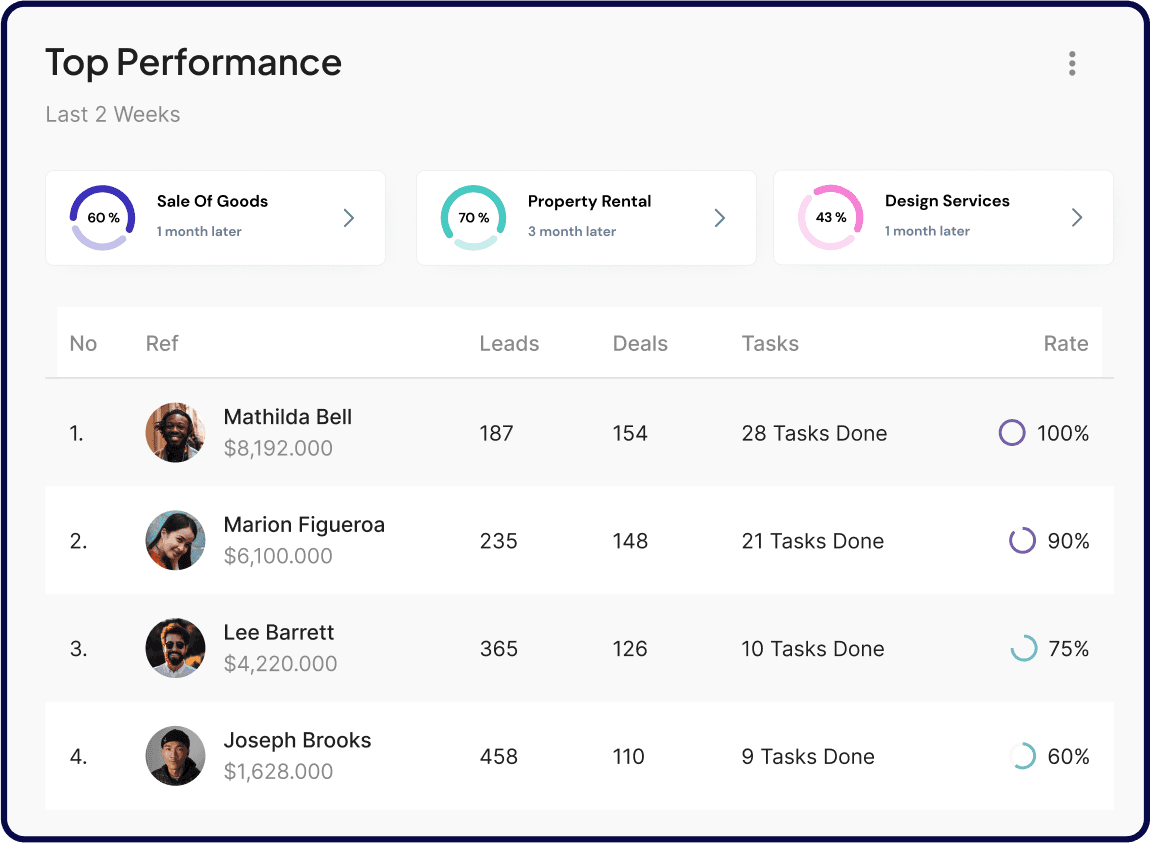
Achivements












How SPYINT Can help ?
How SPYINT Can help ?
With SPYINT, your online presence stays safe , so you can focus on creating without any stress!
With SPYINT, your online presence stays safe , so you can focus on creating without any stress!
With SPYINT, your online presence stays safe , so you can focus on creating without any stress!
With SPYINT, your online presence stays safe , so you can focus on creating without any stress!
Brand Intellligence
Our robust mechanism involves detecting brand impersonations, monitoring brand infringements, and taking down Ponzi schemes.
Anti -Piracy Solutions
Dark web Monitoring






Our beloved clients share their Sharp experience
Our beloved clients share their Sharp experience
"You guys are my digital knight Your AI-powered system instantly flags copyright violations of my content, My audience loves the clean and positive experience on my channel, and it's all thanks to your vigilant protection."

Sassy Poonam
protecting my brand is crucial. Your team was instrumental in taking down fake profiles duping followers in. the name of crypto trading. fostering a positive and supportive community around my brand

Himeesh Madaan
You proactively caught and thwarted a phishing attempt targeting my followers, potentially saving them millions. Your detailed reports give me the insights I need to stay ahead of potential threats and secure my online presence

Crypto Riya
I faced constant online impersonation. Your brand protection services empowered me to reclaim my digital voice. You helped me shut down fake accounts , giving me the confidence to build a thriving online community

Keerthana Merane
"You guys are my digital knight Your AI-powered system instantly flags copyright violations of my content, My audience loves the clean and positive experience on my channel, and it's all thanks to your vigilant protection."

Sassy Poonam
Get experience the modern software service
Sharp provides the best POS services and there are many benefits if you join us. Download now and increase your business.



Get experience the modern software service
Sharp provides the best POS services and there are many benefits if you join us. Download now and increase your business.



Get experience the modern software service
Sharp provides the best POS services and there are many benefits if you join us. Download now and increase your business.